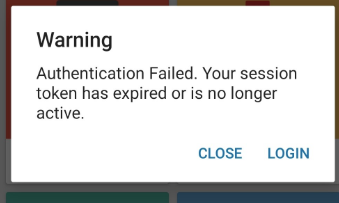
In today’s digital age, tokens play a vital role in various aspects of our lives, from online security to access control. However, what happens when a token expires, and you can no longer utilize it? This article delves into the intricacies of expired tokens, exploring their implications and providing solutions for dealing with them.
Understanding Tokens
Tokens are digital or physical keys that grant access to specific resources or services. They are widely used in a variety of contexts, including authentication, authorization, and payment processing. Tokens can be in the form of passwords, security codes, API keys, or even physical access cards.
Token Expiry: Why Does It Happen?
Tokens have a finite lifespan for security reasons. When a token expires, it means that it is no longer valid for the intended purpose. This expiration is a crucial security measure designed to protect sensitive information and maintain the integrity of systems. Here’s why tokens expire:
- Security Enhancement: Expiry reduces the window of opportunity for malicious actors to misuse a token. It forces users to renew their access, which can thwart unauthorized access attempts.
- Risk Mitigation: As time passes, the risk associated with a token being compromised increases. Expiry ensures that even if a token is stolen, its usefulness is limited.
- Regulatory Compliance: Some industries and regulations mandate token expiration to ensure data protection and compliance with security standards.
Implications of an Expired Token
When a token expires, it can have significant consequences, both for individuals and organizations:
- Access Denied: The most immediate impact is that the user is denied access to the resource or service they were trying to reach.
- User Frustration: Expiry can lead to user frustration, especially if they were in the middle of an important task.
- Security Risks: If not managed correctly, expired tokens can create security vulnerabilities, as users might resort to workarounds to regain access.
- Operational Disruption: In an organizational setting, expired tokens can disrupt operations, leading to downtime and potential financial losses.
Token Expiration Strategies
To manage token expiration effectively, it’s essential to implement the right strategies:
- Configurable Expiry: Allow administrators to set token expiration periods based on the specific use case and security requirements.
- Notification Systems: Implement notification systems that alert users well in advance of token expiration, giving them time to renew or replace the token.
- Grace Periods: Consider implementing grace periods that allow users a limited window of access even after token expiration, preventing abrupt service interruptions.
- Token Revocation: Enable token revocation mechanisms to quickly invalidate tokens in case of security concerns.
Renewing Expired Tokens
When a token expires, it’s not necessarily the end of the road. Users can often renew their tokens by following these steps:
- User Authentication: The user may need to re-authenticate themselves to prove their identity.
- Token Renewal Request: After authentication, users can request a renewal of their token through a secure process.
- Validation and Issuance: The system validates the user’s request and issues a new token with an updated expiration date.
Conclusion
In the world of digital security and access control, tokens are the keys to the kingdom. Understanding token expiration and its implications is crucial for both users and organizations. By implementing effective token expiration strategies and renewal processes, you can navigate the expiration of tokens with minimal disruption and maximum security. Remember, an expired token doesn’t have to mean the end of access; it’s often just a step in the security dance of the digital age.